OneTivi.com — Email phishing continues to rank among the most dangerous online threats for Americans, and understanding an email phishing example can save you from falling victim. A well-crafted phishing email often mimics legitimate organizations—from your bank to social media platforms—making it hard to detect.
In this article, we'll dissect real-world email phishing example scenarios, equipping you with the knowledge to spot red flags and protect your personal information. By reading on, you’ll learn practical tips to outsmart scammers before they can compromise your data.
(toc)
Common Email Phishing Example Scams
Email phishing scams evolve constantly, but certain schemes remain popular because they prey on human psychology. Below, we explore some of the most prevalent email phishing example scenarios targeting United States residents.
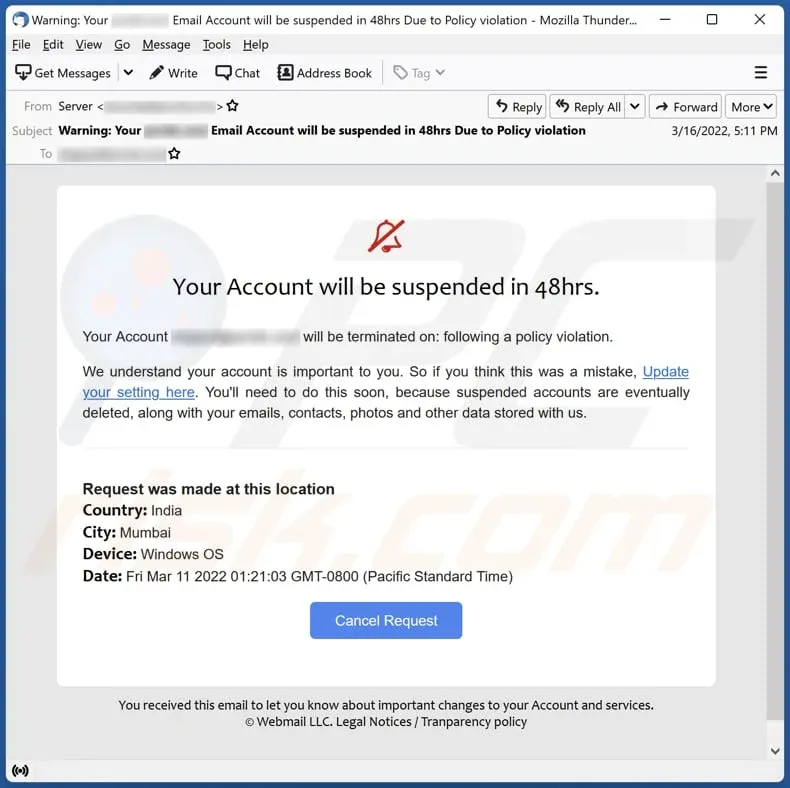
1. The Fake Bank Alert
Investigators report that nearly 40% of email phishing attacks begin with fraudulent banking emails designed to create a sense of urgency. Scammers create emails that appear to come from your bank—complete with official logos, urgent subject lines like "Account Suspended," and a link to "Verify Your Account Now." These messages often cite suspicious activity or unauthorized transactions, pressuring you into clicking a malicious link.
In a typical fake bank alert email phishing example, the email header and footer match a real bank’s formatting, but the sender’s address might slightly differ (e.g., noreply@bankofarnerica.com instead of @bankofamerica.com). Clicking the link directs you to a convincing but fake login page that captures your username and password.
2. The Payment Invoice Scam
Small business owners and freelancers frequently receive invoice-themed phishing emails asking them to pay a past-due balance. In reality, no such invoice exists. Instead, clicking the PDF attachment or embedded link delivers malware to your computer or steals login credentials.
How This Scam Works:
- Spoofed Sender Information: The scammer forges the "From" field to look like it’s from a regular vendor, often by changing a single letter or digit in the address.
- Urgent Payment Requests: The body of the email warns of late fees or service disruptions if payment isn’t made immediately.
- Malicious Attachments: The attached file may look like a legitimate invoice but actually contains a hidden executable (e.g., .exe files disguised as PDFs).
- Fake Payment Portal: The email link might lead to a counterfeit website that asks for your banking login or credit card details.
3. Brand Impersonation (“Business Email Compromise”)
Targeted at companies rather than individuals, business email compromise (BEC) scams exploit trust between employees and executives. Scammers impersonate CEOs or vendors requesting wire transfers or confidential information. In 2023, BEC attacks caused over $2.7 billion in losses globally (source: FBI Internet Crime Report).
In a typical email phishing example of BEC, the scammer studies the company’s organizational chart, finds the CFO’s or CEO’s real email format, and sends a message requiring immediate action. Since it appears to come from someone inside the organization, employees often comply without verifying.
How to Spot an Email Phishing Example in Your Inbox
Becoming aware of the telltale signs of email phishing examples can reduce your risk dramatically. Below, we explain concrete indicators that an email may be fraudulent—so you can act before you click.
Many phishing attempts rely on creating a false sense of urgency or authority. Scammers assume you won’t double-check details when your "bank account is frozen" or your "delivery is pending," and they count on fear to make you react impulsively. By cultivating a habit of verification, you can sidestep these traps and keep your personal data safe.
Things to look out for when analyzing an email phishing exampl:
- Suspicious Sender Address: Carefully inspect the email domain. If it’s missing a letter, has extra characters, or ends in a country code you don’t expect, proceed with caution.
- Generic Greetings: Legitimate companies often address you by name. If the email starts with "Dear Customer" or "Dear User," be skeptical.
- Spelling and Grammar Errors: Professional organizations proofread their communications. Multiple typos can signal a phishing attempt.
- Urgent or Threatening Language: Phrases like "Immediate Action Required" or "Your Account Will Be Closed" are red flags.
- Inconsistent Branding: Check whether logos are low-resolution or if fonts differ from what you normally see from that company.
Preventing and Responding to Email Phishing Example Attacks
Even with vigilance, nobody is entirely immune to ever-evolving phishing schemes. Below are proven strategies for both prevention and response—so you can minimize damage if you ever encounter a real email phishing example.
Organizations such as the Cybersecurity and Infrastructure Security Agency (CISA) recommend a multi-layered defense, combining employee training, technical safeguards, and policy enforcement. On a personal level, regular updates, strong passwords, and a healthy dose of skepticism go a long way.
Before we dive into the actionable steps, here’s why immediate action matters:
- Data Breach Costs: The average data breach in the U.S. costs over $9 million.
- Identity Theft: Victims of phishing have a 45% chance of experiencing identity theft within a year of the attack.
- Recovery Time: Even repairing a credit score after identity theft takes months.
Prevention Techniques:
- Enable Two-Factor Authentication (2FA): Add an extra layer of security so that even if a scammer obtains your password, they can’t access your account without a secondary code.
- Use Email Filters and Security Software: Modern email clients and antivirus programs can detect and quarantine known phishing emails.
- Keep Software Up to Date: Patch your operating system, browser, and applications to close security vulnerabilities that attackers exploit.
- Regularly Educate Yourself and Others: Attend webinars, read official blogs, and perform simulated phishing tests to stay one step ahead of scammers.
Steps to Take If You Fall for an Email Phishing Example:
- Disconnect Immediately: If you clicked a link or opened an attachment, disconnect from the internet to prevent further data exfiltration.
- Change Your Passwords: Update compromised credentials, and if you reuse passwords, change them everywhere.
- Alert Your Bank or Credit Card Company: If you shared financial information, inform your bank right away to freeze your accounts.
- Report the Email: Forward the phishing email to the Federal Trade Commission at spam@uce.gov and to the Anti-Phishing Working Group at reportphishing@apwg.org.
- Monitor Your Credit: Check your credit reports for unauthorized activity. Free annual credit reports are available at AnnualCreditReport.com.
Why Email Phishing Examples Remain Effective
Despite widespread awareness, email phishing examples continue to succeed because they exploit human behavior. Scammers devote resources to crafting messages that look convincing, using data stolen from breaches and social media profiles. They often:
- Personalize Messages: By referencing a victim’s name, job title, or recent purchases, they build credibility.
- Time Attacks Strategically: Scams spike during tax season, Black Friday, and major holidays when users expect lots of emails and may let their guard down.
- Use Sophisticated Malware: Some phishing emails contain zero-day exploits that bypass antivirus software.
Organizations must adopt an adaptive security framework that continuously learns from new threats. On an individual level, vigilance and skepticism are your best defenses.
Conclusion
As cybercriminals become more creative, understanding an email phishing example is essential for safeguarding your personal and financial information. By learning to recognize common phishing scenarios, spot suspicious signs, and react swiftly if compromised, you’ll dramatically reduce your risk of falling prey to these scams. Don’t wait until it’s too late—test your awareness by reviewing old emails, enabling 2FA, and sharing this guide with friends and family. Stay informed, stay aware, and click wisely.
If you found this article helpful, share it with your network and subscribe to our newsletter for the latest security tips and data breach updates.
Frequently Asked Questions
1. What should I do if I’m unsure whether an email is a phishing attempt?
If you’re unsure, don’t click any links or download attachments. Instead, verify the sender’s address, hover over links to see the real URL, and contact the organization directly via a known phone number or website.
2. Can phishing emails still infect my mobile device?
Yes. Mobile phishing is on the rise; attackers craft SMS or email scams specifically for smartphones. Always check URLs, don’t install apps from untrusted links, and keep your device’s operating system updated.
3. How can I report a phishing email to my email provider?
Most providers (Gmail, Outlook, Yahoo) have a “Report phishing” or “Mark as spam” button. Reporting helps improve filters. You can also forward malicious emails to the Anti-Phishing Working Group at reportphishing@apwg.org.
4. Are there differences between spear phishing and general phishing?
Yes. Spear phishing targets a specific individual or organization, often using personal data to seem more legitimate, whereas general phishing is sent en masse. Spear phishing emails are harder to spot due to personalized content.
5. Should I notify my employer if I fall for a phishing scam at work?
Absolutely. Inform your IT or security team immediately so they can contain the breach, change compromised credentials, and assess potential damage to company systems.